- Jul 19, 2019
- 6 minutes
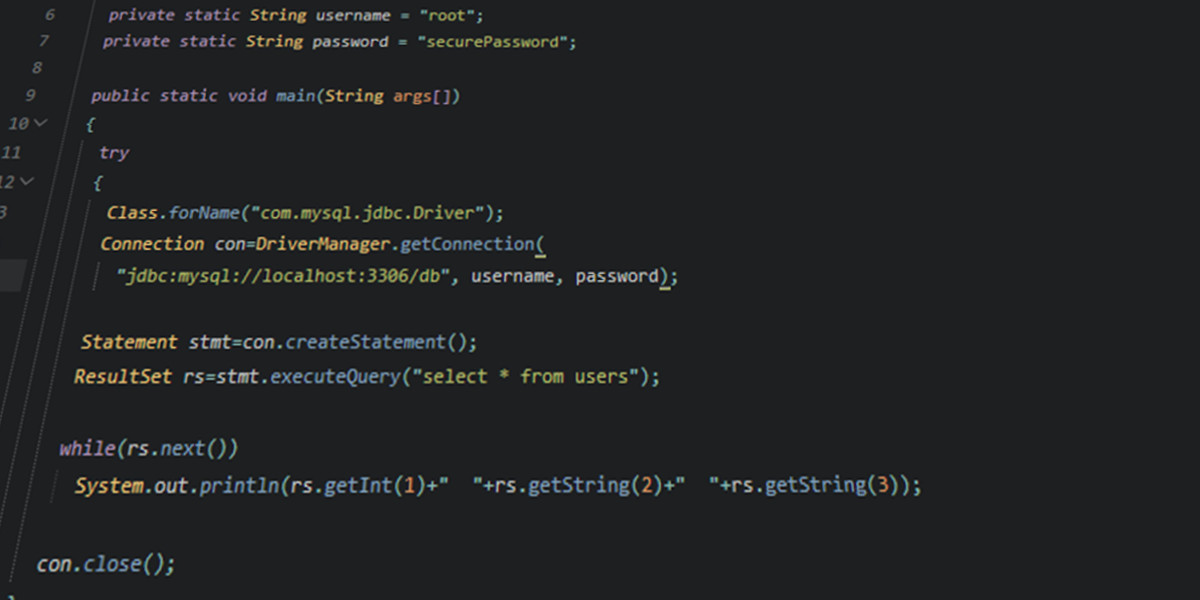
Hardcoded Passwords
Hardcoded passwords… This is a problem quite common, and most of the projects that I get my hands on have a hardcoded password somewhere.
But, what’s the problem of having for example the password of the database in the code?
Well, actually, a lot!
Lets start by the most straightforward …

- Jun 26, 2019
- 3 minutes
Reverse Tabnabbing
Reverse Tabnabbing or also known as Unsafe Target Blank is one of the most underrated vulnerability, and this is the one I like the most. It’s really easy to find an exploitable web application and it’s also quite easy to mitigate.
So what is Reverse Tabnabbing?
When you create a link …
- Jun 17, 2019
- 7 minutes
Insecure Deserialization in Java
Insecure deserialization got in OWASP top 10 in 2017 as most of web applications written in Java and .net where found vulnerable and in most of the scenarios the vulnerabilities got to Remote Code Execution (RCE)
So lets see how this vulnerability works, how to exploit it and how to prevent it. …
- Jun 17, 2019
- 7 minutes
Weak Random
A lot of developers don’t know that regular Random is a weak random implementation. In fact its quite predictable. A lot of code relies on this class to generate passwords, tokens and other security related values, that in fact end up not being secure at all.
I’m going to focus on Java, …

- Jun 17, 2019
- 6 minutes
XML External Entities (XXE)
XML and JSON are two formats ruling the web right now.
Although JSON’s adoption is increasing significantly specially with REST, XML is still widely used.
What most of developers don’t know is that most of the XML parsers out there by following the specification by default have major …





