
- Dec 15, 2025
- 13 minutes
Building MirageVM: A JavaScript Virtual Machine for Code Obfuscation
Modern web applications face a persistent challenge: automated attacks that bypass traditional security measures. Captcha farms and AI-powered tools have made it increasingly difficult to distinguish between legitimate users and malicious bots. Services like anti-captcha and 2captcha can solve a …

- May 7, 2025
- 4 minutes
Bots to the Rescue: How I Built an AI Security Wingman
Security operations teams spend a fair amount of time on repetitive administrative tasks. Answering recurring process questions, manually triaging alerts, guiding teams through procedures, maintaining documentation and tickets. The operational overhead is substantial.
Historically, these tasks …

- May 29, 2022
- 5 minutes
Path Traversal & LFI can be worst than you think
LFI and Path traversal are not a new thing, but what most people don’t understand is the full impact of the vulnerability.
In this post I’ll cover different attack scenarios when exploiting a LFI vulnerability, like enumerating process, dumping environment variables, and on more extreme …

- Nov 11, 2021
- 5 minutes
We are making authentication systems wrong
For a long time I’ve been struggling with the way authentication systems work, as they don’t protect your password as they should. If you search for login best practices, like in OWASP, they’ll tell you things like hashing the password with a strong algorithm, use salt and pepper, …
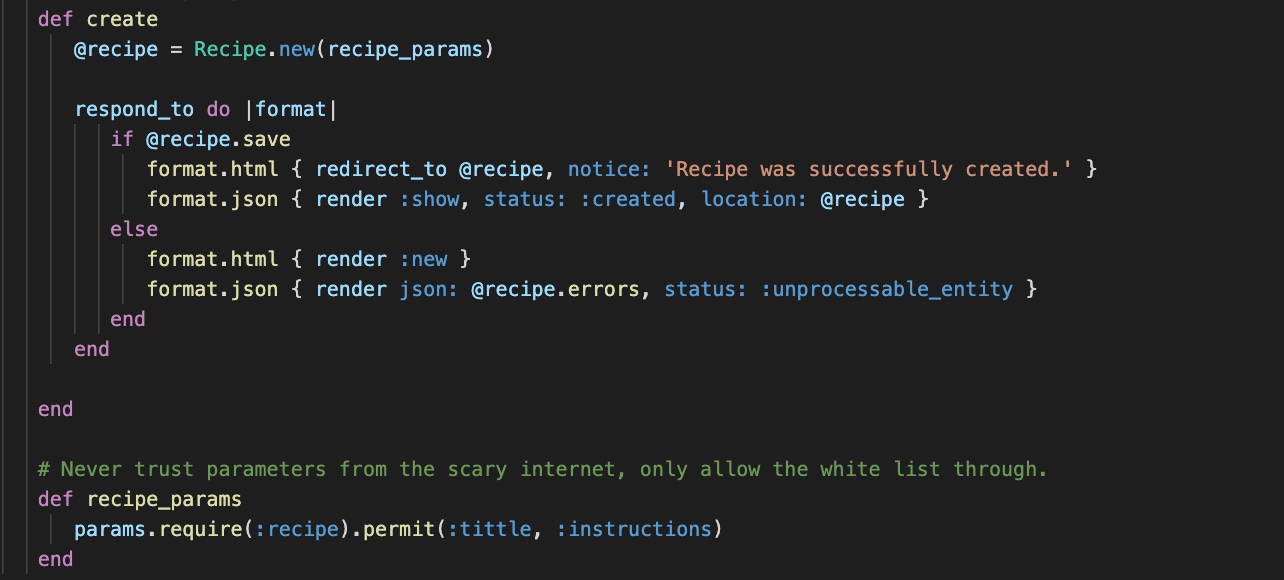
- Jun 13, 2021
- 6 minutes
What is and how to prevent Mass Assignment Vulnerabilities
First time I heard about mass assignment vulnerabilities was a long time ago, when I started learning Ruby & Rails. In fact I learnt a lot, security related back then, as Rails is a quite complex and secure framework, and to properly work with it you should understand the underlying mechanisms. …





